(Deprecated, Bitbucket 7 Only) Configuration of static analyzers
This feature is deprecated in favor of the 'Show Code Analysis in Pull Requests' feature. Please migrate your existing analyzers.
This feature only works on Bitbucket 7, with a single node.
Code Review Assistant shows violations found by static analysis tools in pull requests by using Bitbucket's Code Insights feature.
Currently, it integrates PMD, Scalastyle, JSLint and JSHint. It can also run any external program that can analyze source code and emits line-based violation information for found issues in the program's standard output.
It can also prevent merges of pull requests in case a configurable threshold of violation errors is exceeded.
Configuration of static analyzers
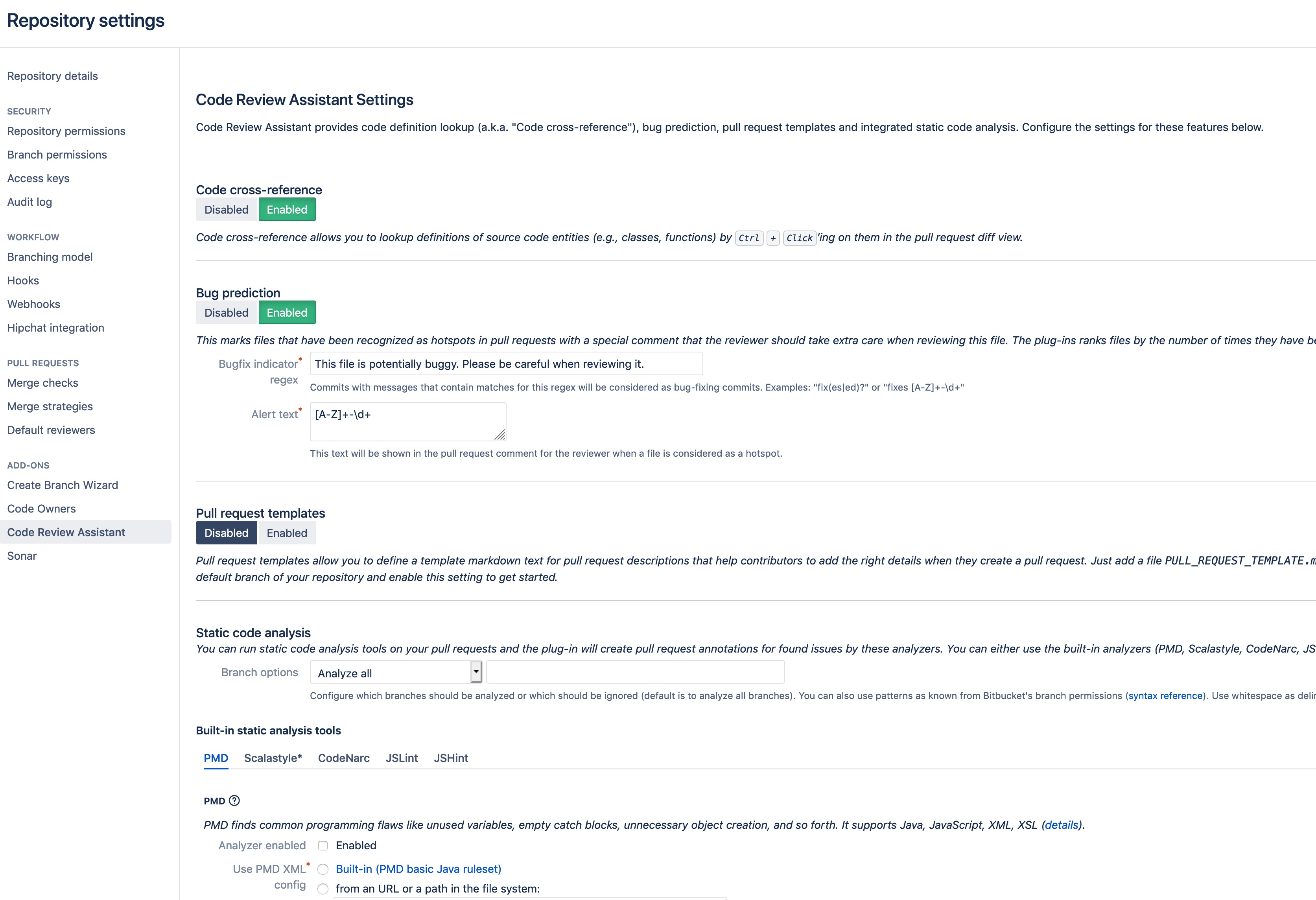
Go to the Bitbucket Server repository you want Code Review Assistant to get executed when pull requests are created. There is a section called "Code Review Assistant":
On this page, you can decide which of the many features of the app you want to use for your repository.
Built-in analyzers
If you want to use static code analysis for one of the built-in analyzers, you can define the following settings for them:
Config file: Use either a built-in (shipped with the plug-in) configuration, specify one by an URL (e.g. if your company shares one by Dropbox), one from the server you run Bitbucket Server on or one from your repository. If you want to use one from your repository, specify the relative path to your configuration file of the chosen analyzer. If your analyzer is PMD and the file is called
pmd.xmllocated in the foldercommon/codequality, then usecommon/codequality/pmd.xmlas the path. Note that this file must be contained in the source branch of your pull request.Violation limit to merge pull request: This is the maximum number of violations with severity level ERROR or FATAL to still be able to merge pull requests. If you don't want to restrict pull requests with violations from being merged, leave this field empty. Note that all of the supported static code analyzers have different kind of severities for the reported errors. Code Review Assistant maps them to the following categories: INFO, WARNING, ERROR, and FATAL:
Violation Type INFO (just for information purposes) WARNING (a potential problem that needs to be investigated) ERROR (a serious violation that results in software faults) FATAL (a fatal error occurred, e.g. the configuration file could not be found or the static code analyzer crashed) Show violation examples (PMD ONLY): PMD provides examples of violations that can help in solving them.
Please note that your config files need to be compatible with the versions of the static analyzers shipped with the plug-in.
Especially PMD introduced quite a few incompatibilities with the latest major version upgrade from 4.x to 5.x. See the FAQ for details.
External customer analyzers
Note that you can also run any static code analysis tool on your code. Please find more details in the external analyzer section of the documentation.
Analysis results within the pull request
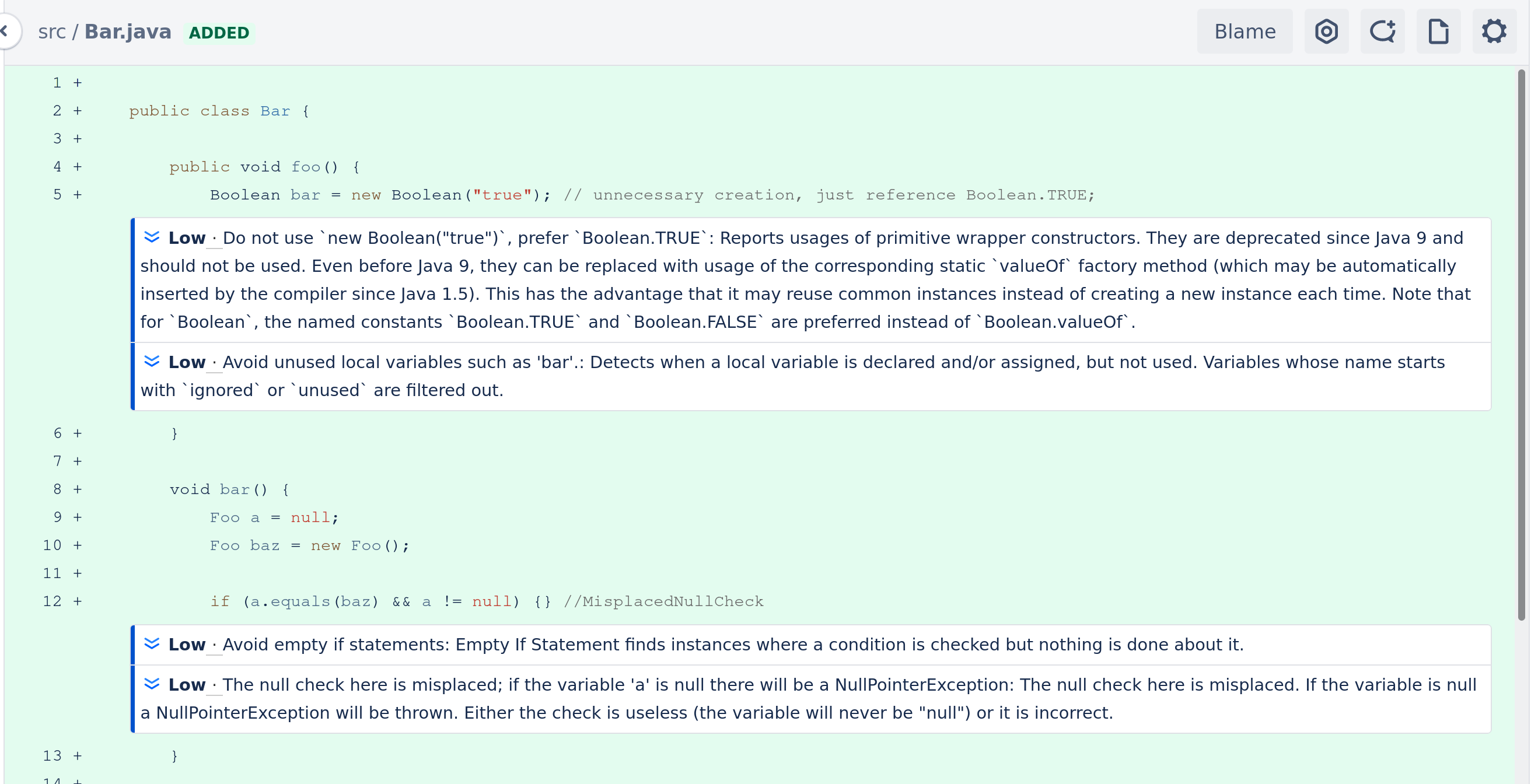
There is no special handling necessary to use Code Review Assistant. Just create pull requests and Code Review Assistant automatically runs the configured static code analyzers on the changed files and reports the violations on the pull request page.
Note that to make code reviews efficient, Code Review Assistant only reports violations occurring in changed and new files of the given pull request.
Here you see an example of a pull request with one violation shown:
You can also see the statistics of the executed static code analyzers in the pull request overview of Code Insights:
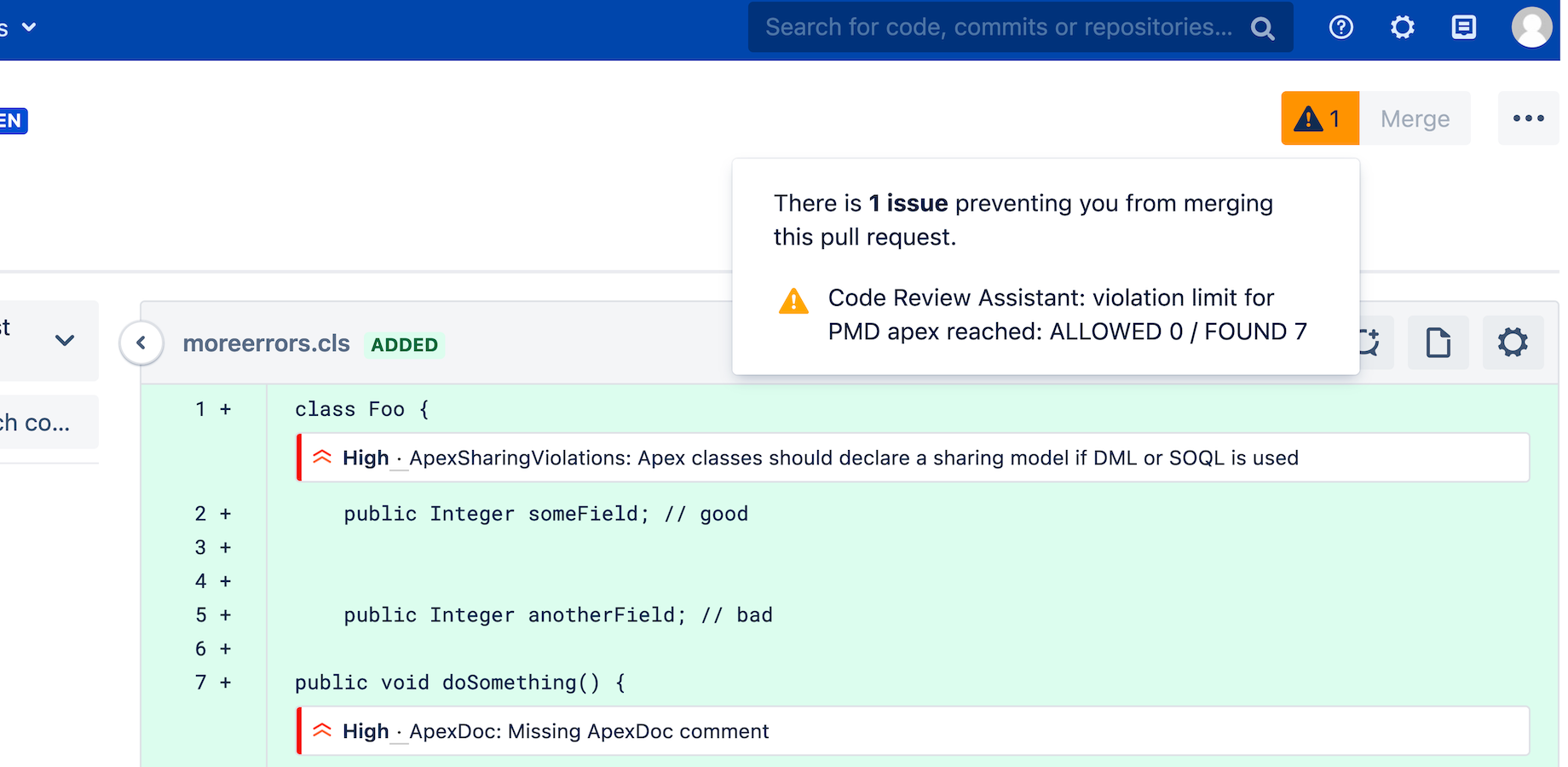
Merge checks to prevent quality issues
When you want to merge a pull request that has more than the configured limit of violations, Code Review Assistant does not allow to merge this pull request:
The next step is to solve the violations. When you are ready, just push the changes and Code Review Assistant automatically runs the static code analyzers again. Once you are below the configured limit, you are allowed to merge the pull request.